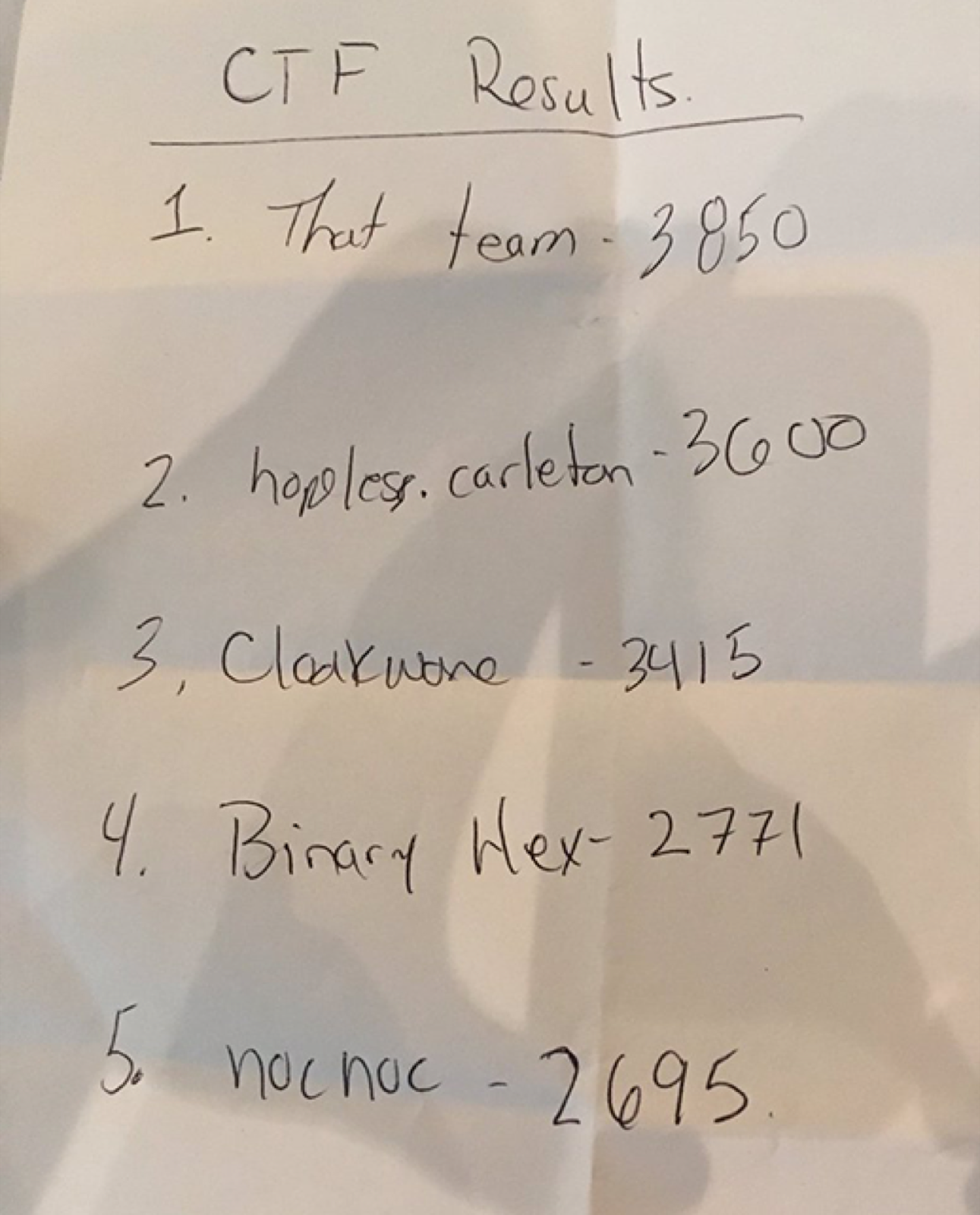BSides Ottawa CTF - Second place!

Last thursday and friday I had the chance to participate in my first professional level CTF at BSides Ottawa. Hopeless.carleton, the team I was on, came second overall with a remarkable 3600 points! We were actually in first place until roughtly the last minute, when “That @Shopify Team” found one more flag putting them 250 points ahead of us. It was a close fight until the end!
One small note
The organizers dropped one final challenge on us with about 2 hours left (thought it only felt like 1/2hr). It was a web challenge which I chose to work on. We were told to get the flag.txt which was located at the root of the box. We were given a ruby webshell on the box however when trying to read the flag we would get permissions denied. Through some investigation I determined that the account “Cyber” which the app was running under was part of the sudoers group however when running sudo cat /flag.txt the web shell would crash when waiting for the interactive input for the password. My teammate thought that this might be a weak creds attack and a nmap scan revealed that SSH was open to the box so all I needed to do was get the password for the Cyber account.
So with 5 minutes left I started trying every possible password from “password” to “admin” to “qwerty” to even “CyberCyberCyber” (the name of the ruby app). After all that I had no luck. With about 30 or so seconds left I noticed that “That Team” got it, so I though let’s just do cat .bash_history to see if they might have left anything useful behind, but they didn’t. After talking to “that team” afterwords it turns out the password for the Cyber account was just Cyber. If I would have gotten that we would have won since the flag was worth 300 points. Moral of the story, always try the username as the password and never use your username as your password.
BSides Ottawa Challenges
In this blog post I aim to cover some of the challenges I managed to tackle and what I learned while breaking them. The challenges are roughly in the order that my team and I managed to break them. I’ll hide the answers and post the challenges as well this way if you would like to try out the challenge you can. Unfortunately I didn’t take pictures of the network ones, so I am unable to discuss them in detail.
CTF-101: A new script for “Office Space”
While writing a new script for Office Space we ran into an error. Can you find it?
- [ OfficeSpace1_50c3dec44908681b0b83d4c41064cef7.txt ]
- [ OfficeSpace2_6c2adf8296719145a5e7558e62287f0a.txt ]
- [ Error_28514fc691bd5b3e0ae1674e3d0b9d34.zip ]
What makes these two scripts different?
Solving this problem was quite trivial. First I started by analyzing the 3 files, we can see two copies of a script for a show and also a zip file that is encrypted with a password. I came to the conclusion that in the scripts there is likely the password for the zip hidden.
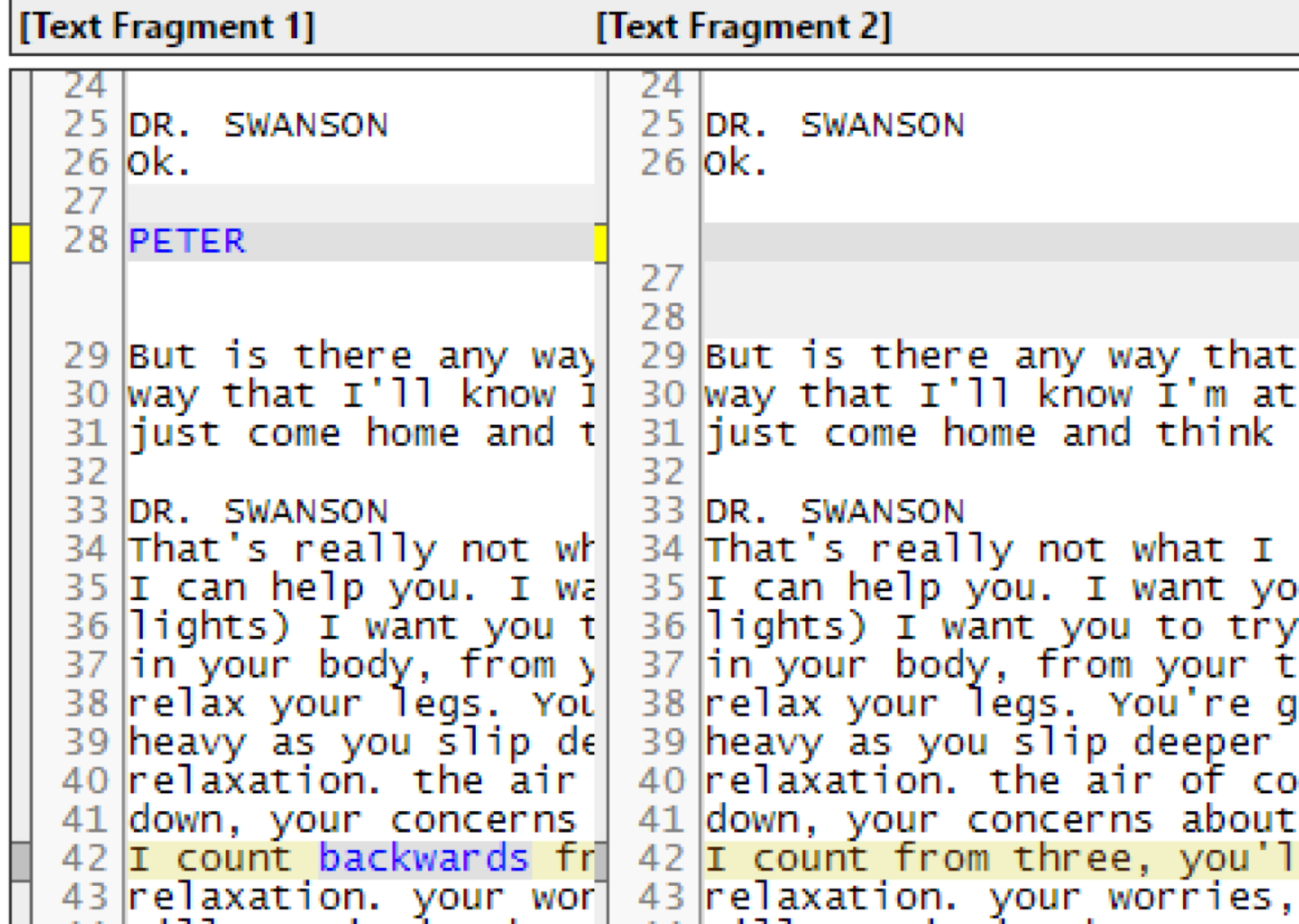
By analyzing the differences between the first and second version of the provided scripts we can see that one of the character’s names PETER is missing from the first script. In the second script we see the addition of the word “backwards”.
Therefore I had concluded that the password to the error.zip file must be PETER backwards: RETEP. After attempting the caps version and it not working I then tried the lowercase version retep and the file extracted revealing:
1 | pcloadletter |
CTF-101: What is this guy pointing at?

What is the filesize so big for such a small image?
To solve this challenge you need to really consider the title of the challenge. Clearly the person is pointing at something but you can’t immediately see what. That indicates that there is more to this image than what we can see. After running binwalk (as per the suggestion of my teammate Nadeem) on the image we can see that there are actually multiple sections.
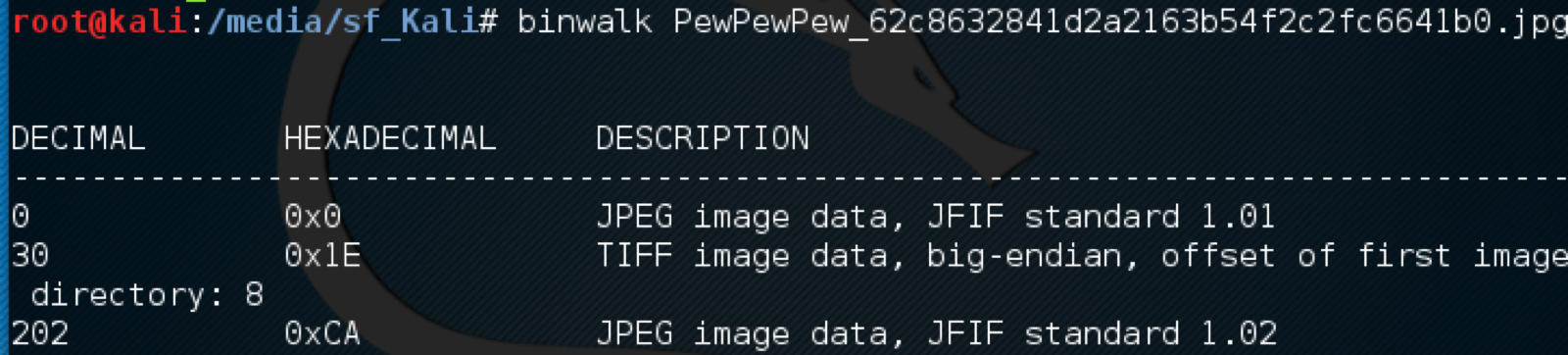 The results of binwalk on the image
The results of binwalk on the imageI attempted to run binwalk -e to automatically extract the multiple portions of the file however that failed. So after running dd if=in.jpg of=out.jpg skip=202 bs=1 we get:
 jigglypuff
jigglypuffCTF-101: Unknown stream incoming
[ unknown.pcapng ]
Can’t you hear the flag?
This challenge wasn’t actually solved until after the CTF was over. @t1v0 and Nadeem solved this one afterwords.
When you open the stream in wireshark you can see that is lots of UDP traffic of the same size between multiple IPs. This is a good indication of the Real Time Protocol being used. Since I know this is RTP go into analyze -> Decode As and choose RTP. This will decode all of the data into something that makes more sense:
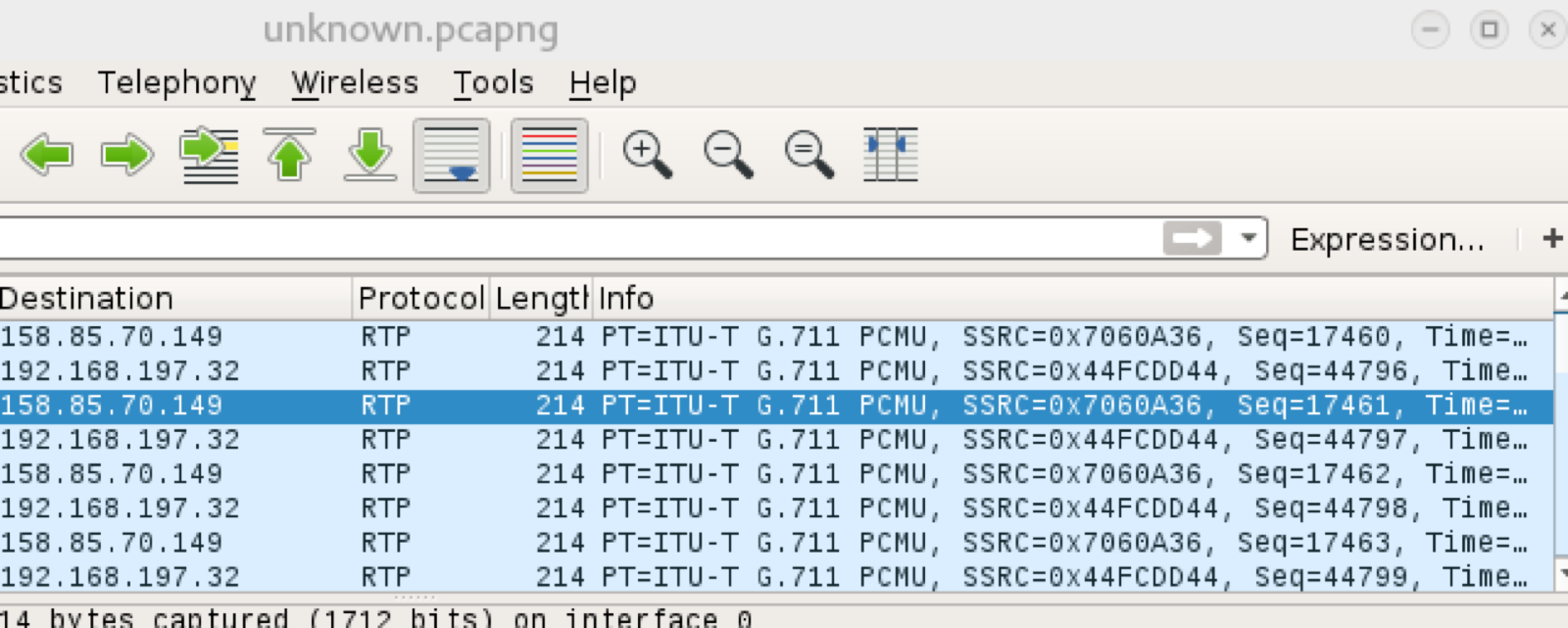 RTP Decoded
RTP DecodedNext you need to analyze the stream, to do that go into Telephony -> RTP -> Stream Analysis. From here you will be prompted to save or play the stream. Here is what it comes out to:
Forensics: Harambe
Harambe looks kind of sad about something.
[ harambe-45f6d15f93c1c7edba4130f87962a2e7ff4445df_081894cb93ac47a1d80f7241d2af0aa4 ]
What is stegsolve?
First things first, let’s figure out what type of file harambe is. After a quick file harambe... I determined that it was an image of harambe:
 Poor Harambe
Poor HarambeMy first instinct with the image was to reverse image search it to see what we can find online. Unfortunately that search didn’t reveal much other than there is a strange black line beside his face. After playing around with a few tools such as binwalk and hexeditors my teammates suggested I try using stegsolve which is a simple program used to solve these kinds of problems. Once I opened stegsolve and messed around with a few of the options I noticed that the Alpha Plane 0 had some black bars across the top and then nothing else… This seemed out of place.
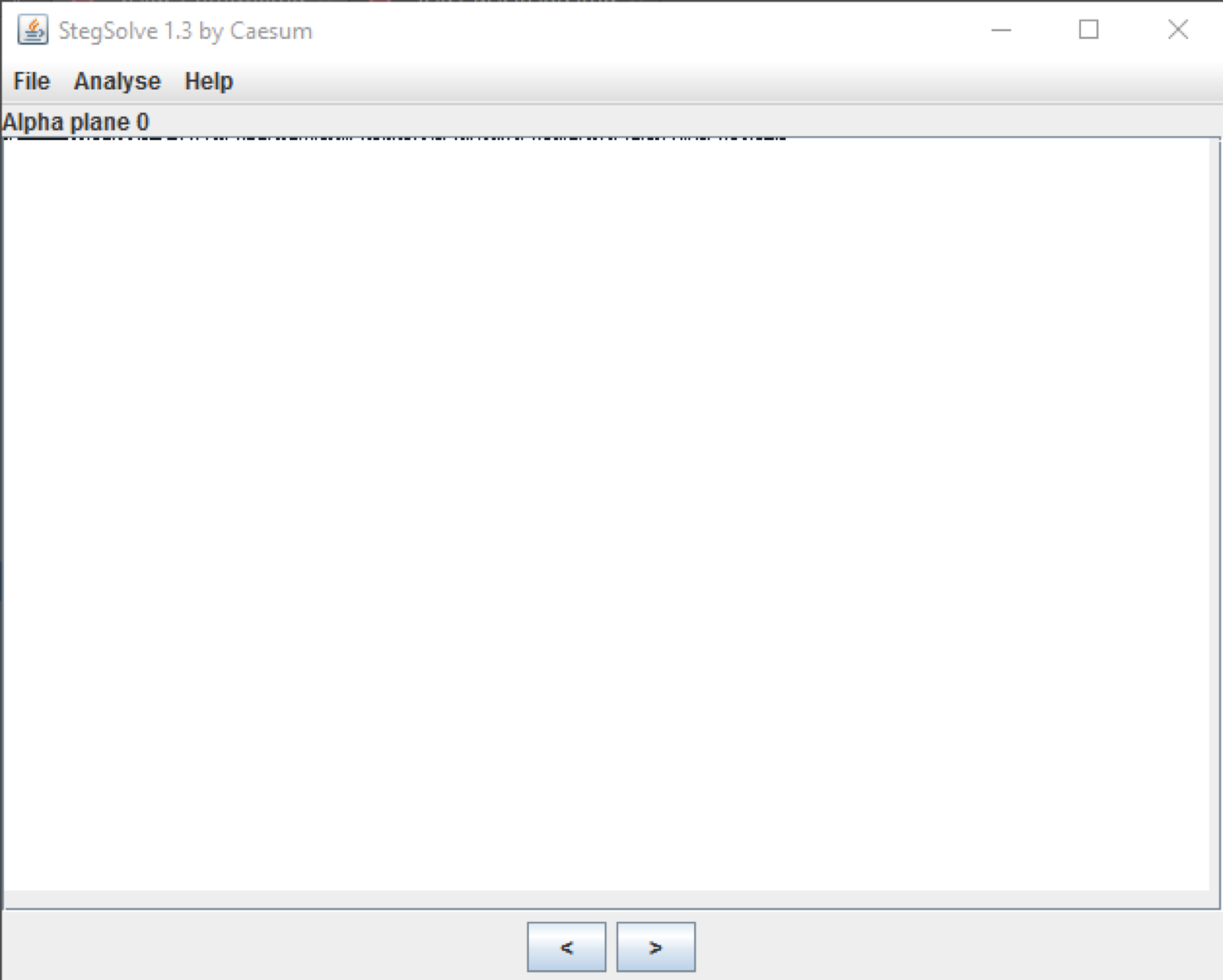 Stegsolve alpha plane 0
Stegsolve alpha plane 0When I noticed this issue I went to the data extract functionality to extract information for the Alpha Plane 0. Unfortunately I didn’t solve this during the event since the copy of Stegsolve I was using was broken and I was unable to view the alpha plane 0 when attempting to extract data. I relied on the tool too much, I could have just made a script… but had it have worked this is what I would have seen:
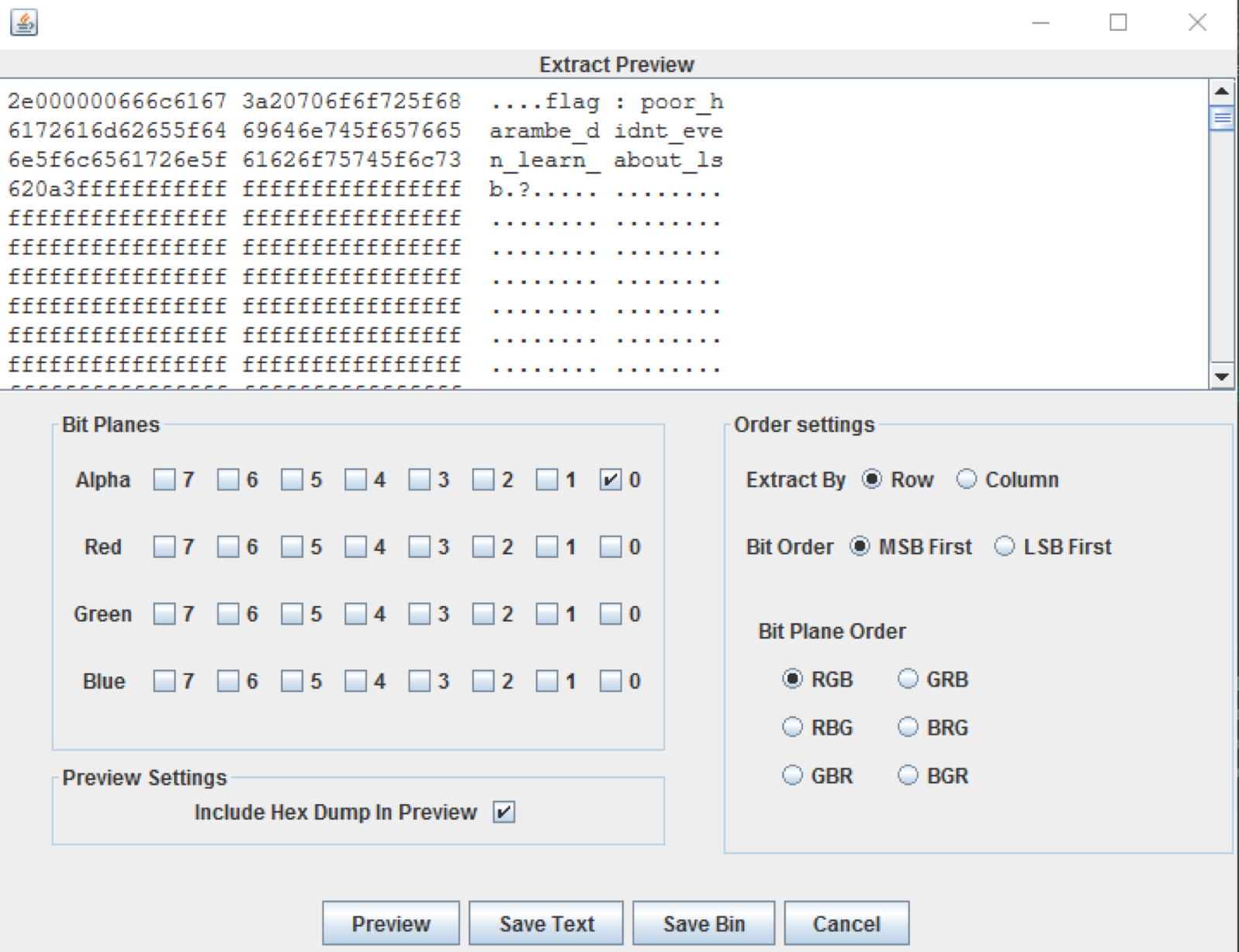 The flag has been found!
The flag has been found!Forensics: Humpty’s Big Party
This invention to the humpty dance looks kind of phishy to me.
[ humpty_dance_838d811304afcd7adcac5306f287182d ]
Mascros, Macros, Macros Everywhere!
Like most other forensics challenges the first thing I needed to do was to determine the file type. By using the file command I was able to determine that this challenge is using a word 2007+ document. After flipping the extension over to .doc and opening the document up I was greeted with a lovely message that went something like: “This document contains macros, we recommend disabling them for your safety”. That was my cue enable macros and view what it is trying to do. When trying to edit the macro your are prompted for a password, so let’s get by this.
I found this nifty little article on stack overflow about bypassing the password by changing DPB to DPx in a hex editor. To do this we first we need to open the .doc in our favourite compression tool AKA winrar and extract word/vbaProject.bin. Next open vbaProject.bin in a hex editor and search for DPB= replacing it with DPx= like so:
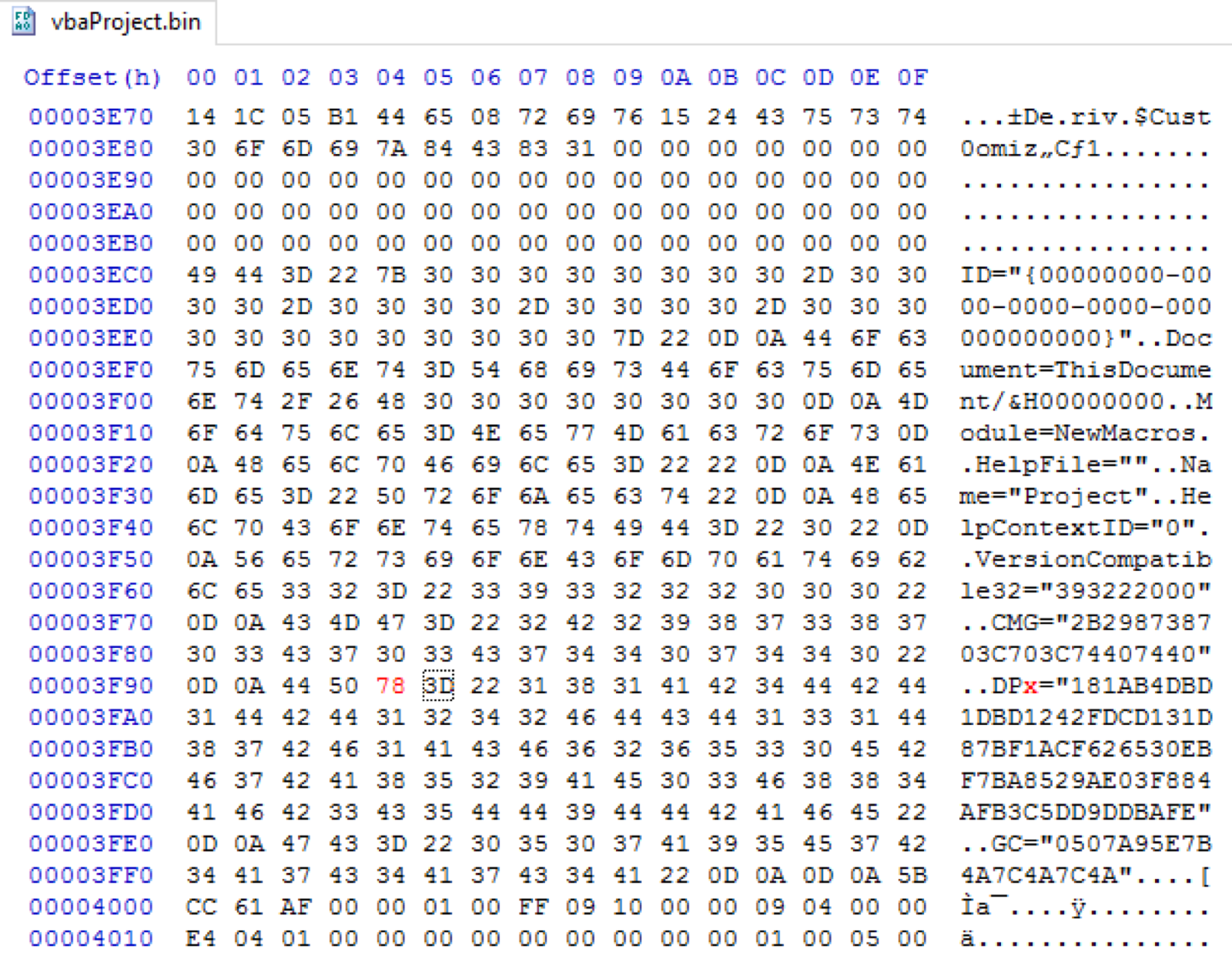 Resetting the PW
Resetting the PWLastly just drag the vbaProject.bin back into the same directory in winrar and re-open the document in word. Now when you open up the document in word and enable macros you will get an error and macros will now be editable:
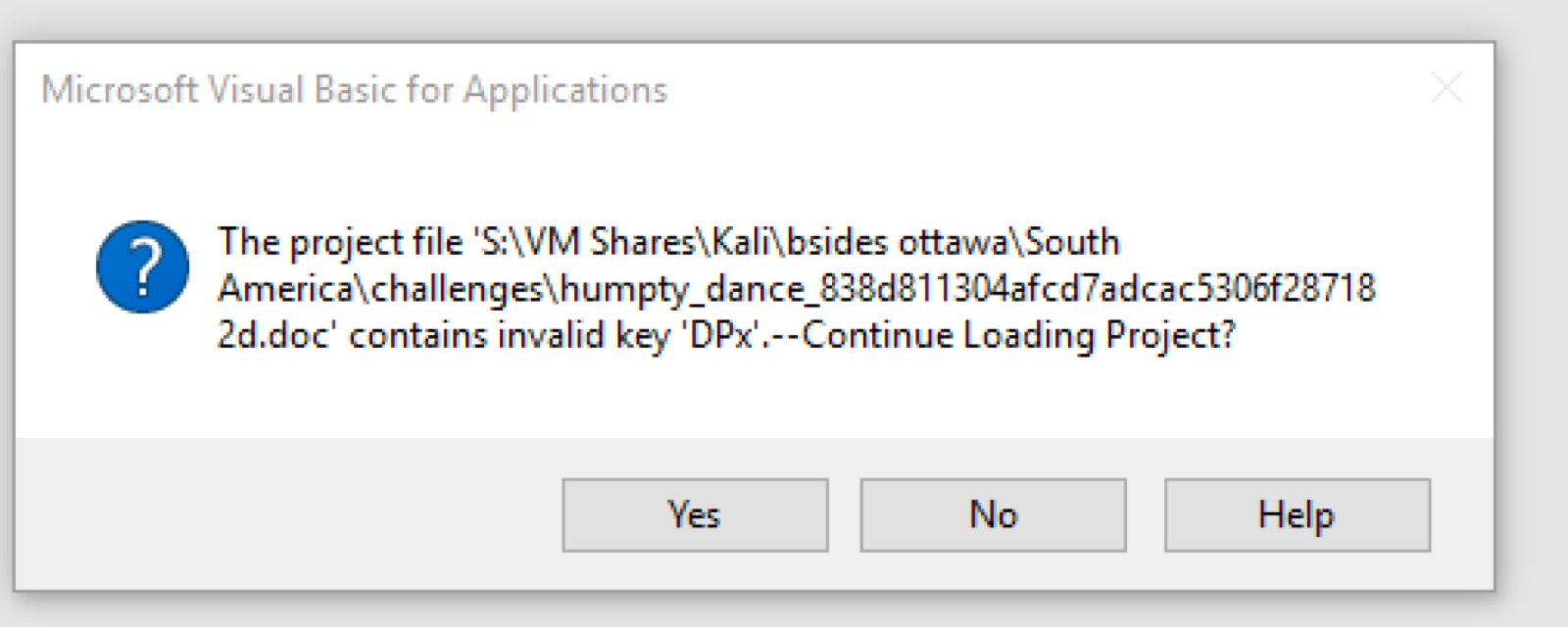 Password error
Password errorIf you open up the macro you get this code:
1 | Sub SpecialerEvent() |
And executing the macro gives:
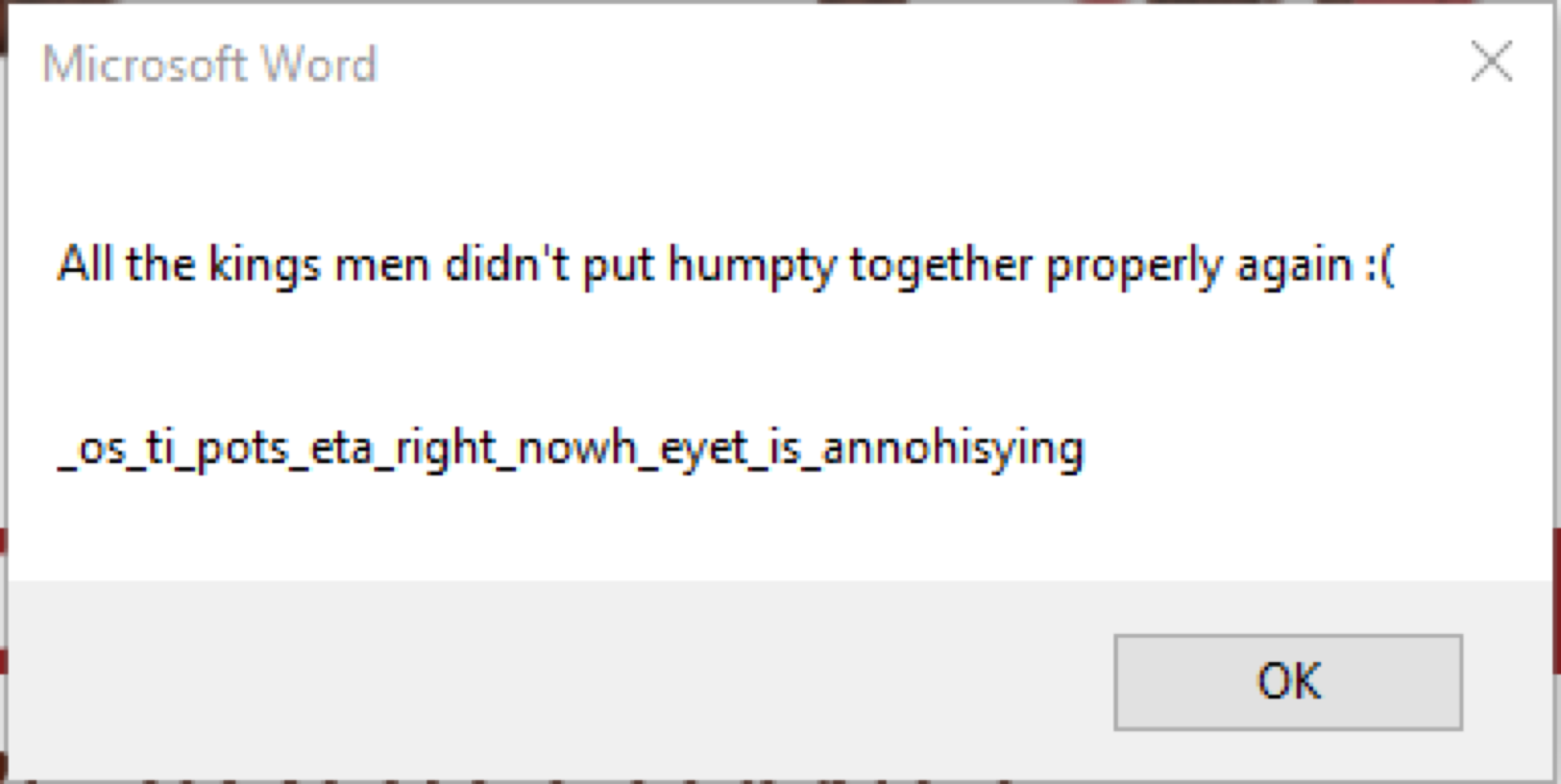 Macro execution
Macro executionFrom the output and some close examination I determined that the arrays were either hex or integers representing letters, so looking at the arrays converted to letters I get:
1 | humpty_1 = Array("_", "e", "t", "a", "h", "_", "e", "y", "e") |
It appears that 1 is reversed, 2 is fine, 3 is fine, 4 is reversed, 5 is fine but 6 & 7 don’t seem to make sense. By analyzing the code I determined that 7 is inserted into 6 making “this_is_annoying”
So now we have eye_hate_right_now_macros_stop_it_this_is_annoying. I don’t remember exactly what the flag was, but it was some variation of that.
Forensics: Mario X
We found a new version of Mario. It is amazing, the graphics are so life like.
[ mario_f539418c5e65405677db05c12e796005.gz ]
Somethings not right with the ending music…
I attempted to solve this during the CTF but was unable to. Credits go to my teammate Nadeem for solving this forensics challenge after the CTF was over.
If you watch the video around 33 seconds into the video you start to hear odd sounds that don’t go with the flow of the music. So if you open the video up in something such as audacity or audition and then press the Spectrogram button (audition it is called “show spectral frequency display”) you will see that the flag has been encoded into the audio:
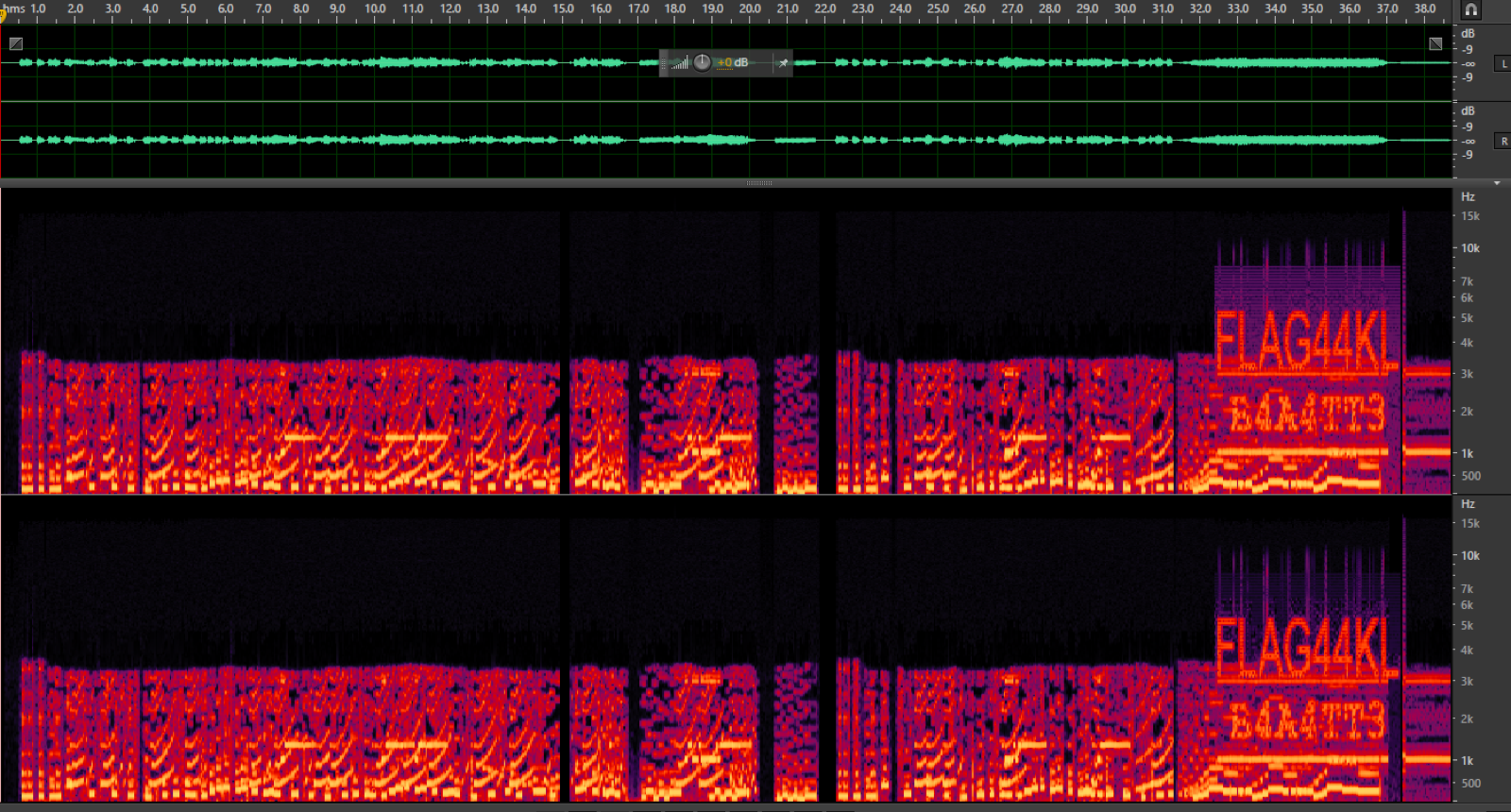 Sneaky...
Sneaky...Old Skewl: Find the flag
Is that some ASCII art?
Copying the text and pasting it into a text editor and then zooming out revealed that there is some ASCII art:
 He-Man and Masters
He-Man and MastersDuring the CTF that was as far as we got. He-man and Masters was not the flag. After the CTF was over the organizers said they found an app which enables encoding a message into an image and then generating ASCII art as the output. This picturesworththousandwords was the app they were talking about. After decoding the text we get: The Flag IS: YoU_Will_NEvEr_FinD_TH1S
That’s all for now! I must say I really enjoyed my time at BSides Ottawa this year and can’t wait for next year! Huge shoutout to Some Random Name for building this CTF!